Computer save become an intricate part of our lives, from desktops to laptops, one would be hard-pressed to find a home without a computing device. Despite its widespread use, most people remain oblivious of the value of a Personal Computer, especially in the control of a cybercriminal.
A hacked computer can be worth a whole lot and be used for different purposes, understanding this can aid you in being more serious about security. An infected PC gives hackers access to email contacts, virtual goods like downloaded music, and account credentials.
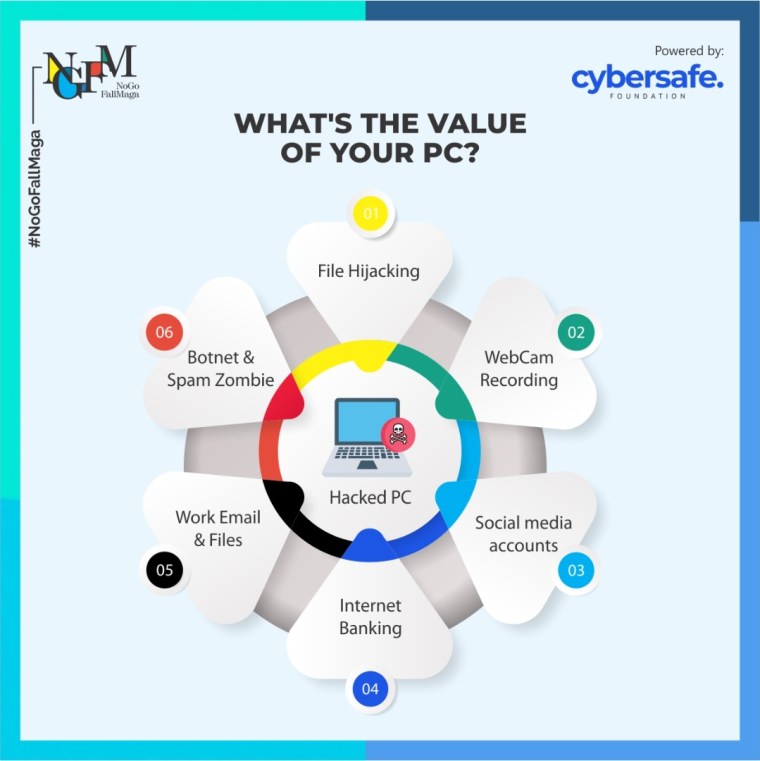
An infected PC also allows criminals to use it as their own personal zombie to host phishing, malware schemes, or as a host to carry out DDoS exploits and attacks, file hijacking, webcam recording, and hijacking social media accounts.
There is so much value in an average user’s PC that it is important you are aware of the risks of being hacked and what stands to be lost. Below are various reasons why a cybercriminal would want to have access to your computing device.
File Hijacking
Hijacking is a type of network security attack in which the attacker takes control of a communication – just as an airplane hijacker takes control of a flight – between two entities and masquerades as one of them, in this case, file hijacking is basically the exploitation of a user’s files by a cybercriminal with access to the user’s computer.
A major way a hacker can access a user’s computer is through the use of ransomware. Ransomware is a form of malware that encrypts the files of its victims. The attacker then demands a ransom from the victim in return for restoring access to the data, another case in which the attacker can hijack users’ files and documents is through the installation of malware from phishing and social engineering.
Webcam Recording
A webcam is one of the most important computer accessories and it can be used in a number of ways. It is also one of the most serious challenges to personal privacy.
If your camera is operated by a second party, they can spy on you, with potentially dreadful consequences. Cybercriminals can exploit a computer’s camera and spy on a user without the consent and knowledge of the user. They lure the user into installing malware, that takes over the webcam of the computer, it is important to be extra careful while on the internet as there is a handful of malware that can take over a user’s webcam.
To check if your webcam has been hacked, please follow the steps below.
* Check the Webcam indicator
* Check the Webcam security features
* Scan for malware on your computer
* Observe the movement of your webcam if you can
* Check running apps and processes
Social Media Accounts
Even though mobile phones are majorly used to access social media accounts, a lot of people still access their social media accounts via a web interface on their PCs. If such a PC gets compromised, the cybercriminal could gain control of the account via such methods as using a keylogger (a type of monitoring software designed to record keystrokes made by a user) to get passwords, doing a password reset (if the cybercriminal already has control of the email associated with the account), or opening from the browser history (this is made possible if the user forgot to log out). A social media account in the hands of a hacker can allow the hacker to carry out impersonation. The hacker can make contacts with friends of the real owner of the account pretending to be the owner and solicit for cash or use the contacts/friends to spread malware or an investment scam.
Internet Banking
Depending on how authenticating into an internet banking platform in the hacked PC is configured, the hacker can reset the password of the internet banking platform.
Remember that most likely, the hacker may already have access to the email in the hacked PC. A password reset using email as a second-factor authentication will enable the hacker to possibly reset the internet backing platform and gain total control of it.
Login credentials can also be obtained via a keylogger, same as above.
Work Email and Files
The pandemic ushered a huge shift to a remote working paradigm, and as a result, people who were not given a dedicated laptop by their company had to make use of their personal computers to access their work emails.
Also, some people often forward to or blind copy their personal emails so as to save certain attachments with a view to working on them later. A compromised work email in the hands of a cybercriminal can be harvested for email addresses that can be sold or used for future phishing attacks.
While access to official documents in emails can lead to exposure of sensitive information and reputational damage for the organization.
Botnet and Spam Zombie
A compromised PC can provide computing power for Cybercriminals to carry out various tasks such as replying to junk email, participating in denial of service attacks, engaging in click fraud, serving as a proxy through which the cybercriminals can route malicious traffic, and solving CAPTCHA challenges to name but a few.
How to Protect Your PC
Protection begins with having the right mindset and realizing that there’s a lot that a Cybercriminal can do with your computing device.
Next, you have to consistently practice good cyber-hygiene such as not clicking unsolicited links or opening unsolicited attachments, and downloading freebies such as pirated software.
Finally, any PC connected to the internet should have a host antimalware program and a firewall.
Contributors:
George Kaduru, Oluwaseun Adio and Archibong Jeremiah.
NB: Opinions expressed in this article are strictly attributable to the authors, George Kaduru, Oluwaseun Adio and Archibong Jeremiah and do not represent the opinion of CrossRiverWatch or any other organization the author works for/with.
This article which is meant to guide the digital community on activities of cybercriminals by the NoGoFallMaga Movement.
NoGoFallMaga is a national movement of young people, working to combat preventable digital fraud with consumer-centered sensitization and education. Digital fraud in this context includes, email deception, phone-based scams, online fraud – particularly where cybercriminals impersonate trusted organizations. We will leverage fun experiences and content, to catalyze the decline of cyber-related fraud, one trickle of knowledge and advice at a time.